We are tracked everywhere online—by companies that want to sell us things and by governments that want to watch us. Every website we visit, every message we send, creates a digital record. Because of this non-stop surveillance, digital privacy has become a major worry. Tools like VPNs are now essential for users who want to be private and secure on the internet.
When you choose a VPN, you might look at its features, like fast servers or strong encryption. But the most important factor is its jurisdiction. This is simply the country where the VPN company is legally set up and operates. The jurisdiction is crucial because it decides which laws the VPN must obey. If the country has laws that force companies to log (record) user data and hand it over to the government, that VPN must comply, even if it promises a "no-logging" policy.
Think of jurisdiction as the final line of defense, which is stronger than any technical feature. A VPN can use the strongest encryption available, but if it is legally based in a country that belongs to an intelligence alliance (like the Five Eyes group), the government can legally demand access to user logs. A technically secure VPN in a bad legal location is still unsafe. For true protection, you need a VPN located in a privacy-friendly country that has no mandatory data retention laws. This legal protection is the best way to ensure your data stays private.
VPN jurisdiction explained
Understanding a VPN's legal posture involves looking at three distinct, yet interconnected, layers. Relying on just one layer can leave your privacy exposed.
1. VPN Company Jurisdiction (Legal Home)
This is the most important factor. It refers to the country where the VPN service is legally incorporated and where its central operations are managed. This jurisdiction sets the fundamental legal rules. For example, a company based in Panama (which has strong privacy laws and is outside intelligence alliances) is safer than a company based in the UK (a Five Eyes member with mandatory data retention rules). The company's legal home determines its exposure to government warrants and compulsory data requests.
2. VPN Server Locations
This refers to the physical location of the servers you connect through. While the server location is vital for accessing geo-blocked content (e.g., using a US server to watch Netflix US), its privacy protection is secondary to the company's jurisdiction. Servers physically located in a country with strong data laws may offer better protection, but if the parent company is forced to log data by its home jurisdiction, the server's location might offer only limited defense, especially in the event of physical seizure or remote access warrants enforced against the parent company.
3. Data Processing Laws (Governing Principles)
These are the specific data protection and privacy statutes in the company’s jurisdiction (e.g., GDPR in Europe). These laws determine:
-
What type of data the VPN is allowed to collect (or is forbidden from collecting).
-
How long the VPN can store the data (data retention limits).
-
The legal process required for governments or police to access that data. For maximum privacy, a VPN should be governed by laws that explicitly prohibit mandatory data retention and require a high legal standard (like a court order) for any data requests.
While VPN privacy laws and data retention laws clash because data retention mandates require ISPs and VPNs to log user activity (IPs, connection times, sites visited) for governments, while VPNs aim to encrypt and hide that data, making reliable "no-log" VPNs often locate servers in privacy-friendly countries (like the Netherlands) to avoid these laws, though VPNs must still comply with laws where they operate and can be compelled to log, especially in "Five Eyes" nations, undermining privacy.
Why Jurisdiction is Paramount: Legal Frameworks Trump Encryption
The legal environment is the single biggest vulnerability for any VPN service. No matter how advanced the technology is, the country's laws provide the ultimate pathway for government interference.
1. Mandatory Data Retention: The Core Threat to No-Logging Policies
The core threat to a VPN's "no-logging" policy comes directly from the law. Many countries, particularly those in intelligence-sharing blocs, mandate that communication providers (which can include VPNs) must log specific types of metadata or user activity for extended periods. If a VPN is based in such a country, its marketing promises are meaningless; it is legally required to retain data, effectively making it an extension of state surveillance. A privacy-friendly jurisdiction, conversely, legally forbids forced data retention.
2. Government Access Powers and Surveillance Capabilities
Jurisdiction determines the power a government has to compel a company to act. In countries with aggressive surveillance laws, a government can issue warrants or subpoenas that force a VPN company to turn over logs, actively monitor users, or even install backdoors into their network infrastructure. This access is granted regardless of the technical encryption in place. Choosing a jurisdiction that respects constitutional privacy rights and requires high-level judicial oversight (like a supreme court order) for data access is paramount.
3. Gag Orders & Transparency: Why Secret Surveillance Warrants Fail Trust
One of the most insidious threats in high-surveillance jurisdictions is the use of "gag orders." A gag order is a legal tool that simultaneously forces the VPN company to comply with a data request and prohibits the company from telling the public or its users about the request. This means a VPN could be compromised without ever being able to warn its customers. Privacy-friendly jurisdictions often have strong transparency laws or constitutional protections that limit or forbid the use of such secret orders, ensuring the VPN can maintain its integrity and communicate legally tested requests to its user base.
How VPN jurisdictions have failed users
To underscore the importance of jurisdiction and operational integrity, here are five notable incidents where VPN services compromised user privacy, either through technical failure, internal leaks, or legal compulsion.
-
IPVanish Cooperates with US Authorities (2016):
-
The Issue: Despite marketing itself as a strict "zero-logs" service, the US-based VPN provider, IPVanish, was served a legal subpoena by the Department of Homeland Security in a criminal investigation and subsequently handed over connection logs (including connection times and IP addresses) belonging to a suspect.
-
The Lesson: A "no-logging" policy is meaningless if the company's jurisdiction is a high-surveillance country (like the US, a Five Eyes member) that can legally compel the company to record and surrender data.
-
Seven Simultaneous VPN Leaks (2020):
-
The Issue: A massive data leak involving 1.2 terabytes of user data from seven affiliated free VPN services (including UFO VPN, Fast VPN, and Super VPN) was found exposed on a public server. The leaked data included user PII (Personally Identifiable Information) like email addresses, clear-text passwords, and detailed user activity logs, directly contradicting their no-logging promises.
-
The Lesson: Many free or lower-tier VPNs not only fail to protect user data but actively log and retain highly sensitive information, demonstrating a fundamental breach of trust and a severe lack of security infrastructure.
-
PureVPN Logs Handed to the FBI (2017):
-
The Issue: PureVPN, which was based in Hong Kong at the time and claimed a no-logging policy, was compelled by the FBI to hand over identifying connection logs (including original IP addresses) that led to the arrest of a cyberstalking suspect in the US.
-
The Lesson: Even VPNs in seemingly neutral jurisdictions may comply with legal requests from powerful international law enforcement agencies (like the US) if the legal mechanism allows, or if they secretly retain some form of connection logs, prioritizing legal compliance over their advertised promises.
-
Hola VPN's Botnet Scandal (2015):
-
The Issue: Hola VPN, a popular service, was discovered to be secretly routing its free users' traffic through a P2P (Peer-to-Peer) network and selling their idle bandwidth to third-party customers through its sister company, Luminati. This effectively turned free users into exit nodes, making them potentially liable for the actions of others using their IP address.
-
The Lesson: Services, particularly "free" ones, often monetize users by compromising their security and privacy in ways that go far beyond simple logging, such as exploiting their network resources for profit.
-
NordVPN's Legal Transparency Clarification (2022):
-
The Issue: Following past controversies, NordVPN clarified its position, stating that while it guarantees a zero-log policy for traffic data, it must comply with any data requests that are legally binding under the laws of its jurisdiction (Panama), should all legal appeals fail. While this involves non-traffic data (like payment info/email), it highlights that no company operates above the law.
-
The Lesson: Even highly audited, privacy-focused VPNs must bow to the legal authority of their home jurisdiction. This reinforces the principle that the company's legal home is the ultimate arbiter of what data it must potentially surrender, making a privacy-friendly jurisdiction paramount.
The Surveillance Alliances: Understanding 5, 9, and 14 Eyes VPN Risk
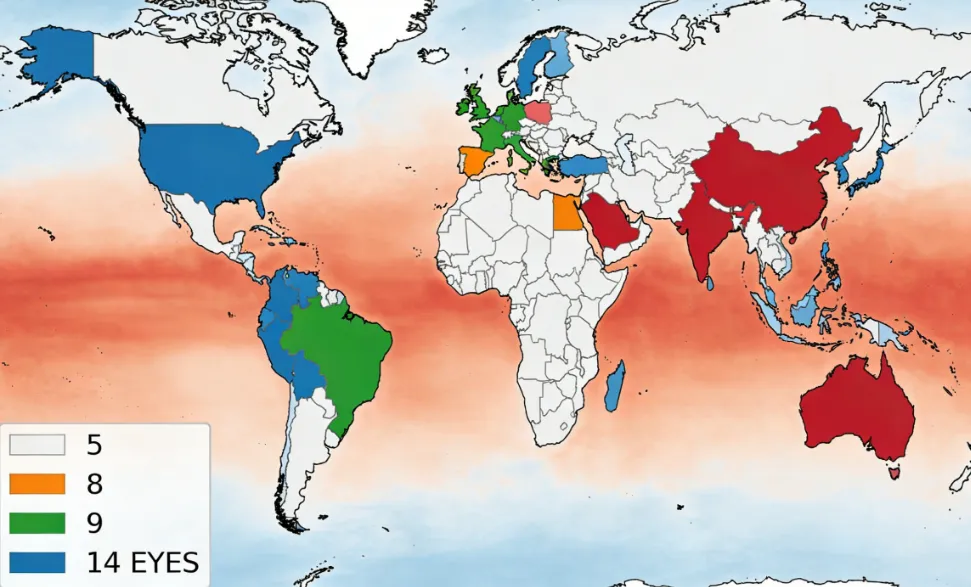
The greatest legal risk to a VPN’s no-logging policy comes from global intelligence-sharing agreements. These alliances allow member countries to legally bypass domestic restrictions by requesting data from a partner nation, creating a significant privacy loophole.
A. What are the Five Eyes (FVEY)? (US, UK, Canada, Australia, New Zealand)
The Five Eyes alliance is a post-WWII intelligence agreement established by the UKUSA Treaty. Its core members are the United States, the United Kingdom, Canada, Australia, and New Zealand.
-
Purpose and Data Sharing Mechanisms: The primary purpose of the FVEY is comprehensive signal intelligence (SIGINT) gathering and mutual data sharing between the five nations. This means that if the US government cannot legally monitor one of its own citizens (due to constitutional protections), it can request the UK's GCHQ to monitor that individual and share the collected data back to the US. This circumvents domestic laws, creating a powerful surveillance apparatus.
-
Impact on VPNs Headquartered in These Countries: VPN providers based in FVEY countries are subject to the domestic laws of that country, which often include mandatory data retention requirements and broad government surveillance powers. Crucially, even if the VPN is not directly served a warrant by its local government, a partner FVEY country can request the data on their behalf. If the VPN were to have logs, they would be legally compelled to surrender them.
B. The Nine Eyes and Fourteen Eyes: Expansion of Intelligence Sharing
The surveillance network extends beyond the FVEY to include broader cooperation frameworks:
-
Nine Eyes: Includes the FVEY countries plus France, Denmark, the Netherlands, and Norway.
-
Fourteen Eyes (SIGINT Seniors Europe): Includes all Nine Eyes countries plus Belgium, Germany, Italy, Spain, and Sweden.
While data sharing is less frequent and formal than within FVEY, these expanded alliances represent a significant network of governmental bodies willing to share surveillance information. A warrant or data request originating in a Fourteen Eyes country can potentially be shared across the entire bloc.
C. Jurisdictions to be Wary Of: Why a VPN in an "Eyes" Country Carries Inherent Risks
If a VPN is legally headquartered in any country belonging to the 5, 9, or 14 Eyes alliances, it carries an inherent and non-negligible risk, regardless of its technical features.
-
Mandatory Data Retention: Many of these nations (especially the UK and Australia) have broad and mandatory data retention laws that can force any communications provider to log metadata.
-
Mutual Legal Assistance Treaties (MLATs): These treaties facilitate the rapid exchange of evidence and data, allowing intelligence agencies to easily and legally request user data from a VPN's home jurisdiction.
-
Gag Orders: Governments in these blocs frequently use secret court orders and national security letters (NSLs) to compel companies to cooperate without informing the public or the user.
For optimal privacy, users should prioritize VPNs based in countries strictly outside of these intelligence alliances, which legally prohibit mandatory data logging.
The 5, 9, and 14 Eyes Alliances: What They Mean for Your VPN Choice
Best VPN not in 14 Eyes: For the best VPNs outside the 14 Eyes, focus on providers in privacy-friendly countries like NordVPN (Panama), Proton VPN (Switzerland), Mullvad (Sweden), and ExpressVPN (BVI), offering strong security, audited no-logs policies, and fast speeds, with top picks often being NordVPN for overall, Mullvad for privacy, and Proton VPN for free options.
Privacy-Friendly VPN Jurisdictions: Safest Countries for VPN Headquarters
The best way to guarantee your privacy is to choose a VPN provider that is legally incorporated in a country with minimal government surveillance and robust data protection laws.
A. Criteria for a Privacy-Friendly Country:
-
Strong Constitutional Rights Protecting Digital Privacy: The country's foundational legal documents must include explicit protections for citizen privacy, requiring high legal standards (like warrants issued by a supreme court) for any electronic surveillance or data seizure.
-
No Mandatory Data Retention Laws: The jurisdiction must explicitly prohibit telecommunication providers (including VPNs) from mandatorily logging or storing user metadata and traffic logs. This legally allows the VPN to maintain a true "no-logs" policy.
-
Stable, Independent Legal System: The country must possess a stable democratic government and a judicial system that operates independently from the executive and legislative branches. This independence ensures that legal challenges against government data requests are fairly judged.
B. Key Recommended Jurisdictions:
-
Panama: This Central American country is often cited as a top privacy jurisdiction due to its strict data protection laws and its political neutrality. Crucially, Panama is not a member of any of the 5, 9, or 14 Eyes alliances.
NordVPN (Audited) - Run by Tefincom S.A. NordVPN operates under the jurisdiction of Panama, a legal foundation chosen specifically to support its "no-logs" policy and enhance user privacy protections. This location offers two primary strategic advantages: it lacks mandatory data retention laws and remains independent of major international intelligence-sharing alliances.
Surfshark (Audited) - Run by Surfshark B.V. (registered in the Netherlands but legally structured through Panama)
-
British Virgin Islands (BVI): The BVI is an independent, self-governing jurisdiction with a powerful Supreme Court. Any legal requests for data must pass through this court, which often sets a high bar for warrants, providing an extra layer of defense against foreign legal demands. The British Virgin Islands (BVI) offers strong privacy for VPNs due to its autonomy, lack of data retention laws, and non-membership in intelligence-sharing alliances (like Five Eyes). New data protection laws (DPA 2021) provide a framework similar to GDPR, requiring consent and safeguards for data transfers, but VPNs with strict "no-logs" policies offer high privacy as they don't store data to hand over, requiring foreign governments to get a BVI High Court order, which is difficult.
ExpressVPN (Audited) - Run by Express VPN International Ltd.
-
Switzerland: Known globally for its financial privacy, Switzerland also has exceptionally strong legal frameworks protecting digital privacy. While in Europe, its specific federal laws and independent status keep it separate from the EU's past mandatory data retention directives and outside the "Eyes" alliances.
ProtonVPN (Audited) - Run by Proton AG, based in Geneva
VyprVPN - Owned by Golden Frog, incorporated in Switzerland
-
Romania: The country has a proven track record of fighting mandatory data retention. Its courts have actively struck down EU directives requiring data logging, making it a legally hostile environment for mass surveillance programs.
CyberGhost - Run by CyberGhost S.R.L. (but owned by Kape Technologies, a UK company)
-
Iceland: Iceland is a global leader in press freedom, human rights, and data protection. Its laws and constitutional culture provide a highly protective environment for digital communication and anonymity, making it a haven for journalists and privacy advocates.
High-Risk Jurisdictions (Countries to Avoid)
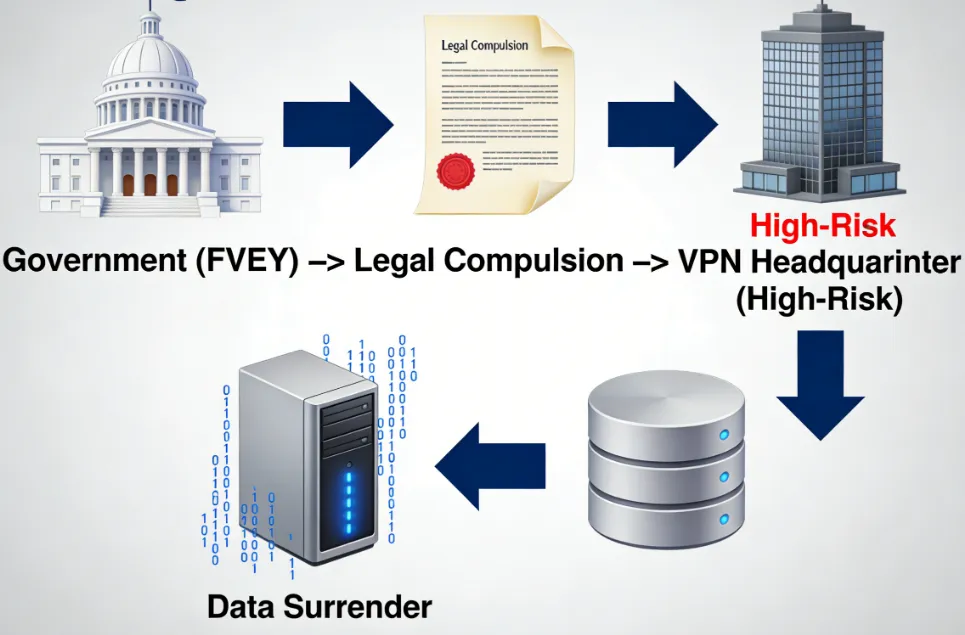
These countries are universally considered poor choices for a VPN's legal home due to aggressive government surveillance programs, intrusive laws, and/or mandatory data retention requirements.
A. The United States (FVEY Member)
The U.S. has a pervasive history of government surveillance, largely managed by the NSA (National Security Agency), as famously revealed by Edward Snowden. U.S.-based VPNs operate under significant legal pressure.
-
Aggressive Use of Warrants and Gag Orders: U.S. law allows the government to issue National Security Letters (NSLs) and warrants that can compel a VPN to log user data, monitor activity, and surrender records—often accompanied by gag orders that forbid the company from disclosing the data request to the public or the affected users.
-
MLATs and International Requests: As the leader of the Five Eyes alliance, the U.S. is heavily involved in international data-sharing, often requesting data from other allied nations to bypass its own domestic limitations.
B. The United Kingdom (FVEY Member)
The UK has some of the most intrusive surveillance legislation in the democratic world.
-
Highly Intrusive Surveillance Laws: The Investigatory Powers Act (IPA), or "Snooper's Charter," forces internet service providers (ISPs) and potentially VPNs to store connection logs for up to a year and grants government agencies broad powers to access and monitor these communications data.
-
Interception Capabilities: The IPA also authorizes bulk data collection and interception, making the UK an extremely risky legal environment for any privacy-focused service.
C. Other High-Risk Areas (e.g., Australia, China, Russia)
-
Australia (FVEY Member): Australia has passed laws that compel companies to assist law enforcement in accessing encrypted communications. Their metadata retention laws are severe, requiring telcos to store vast amounts of data.
-
China and Russia (Authoritarian Regimes): VPNs operating in or having data infrastructure in these countries are subject to direct state control and mandatory data access. The goal of the state is surveillance and censorship, making any local "no-logs" claim unreliable or impossible to enforce against the government.
How to Choose a VPN Based on Jurisdiction
Making an informed choice requires synthesizing the legal risks (like the Eyes alliances) with the technical promises (like a no-logs policy). Follow these steps to select a provider that truly protects your privacy.
A. Prioritize a Company Located Outside of the 14 Eyes Alliance
This is the single most important rule. If a VPN is based in any of the 14 Eyes countries (especially the core Five Eyes members), its legal vulnerability is high. Choose a VPN legally headquartered in a privacy-friendly jurisdiction (such as Panama, BVI, or Switzerland) to ensure maximum legal protection against mass surveillance requests.
B. Look for a Proven No-Logs Policy
A "no-logs" claim in marketing is insufficient. Look for concrete proof, specifically:
-
Warrant Canary: A public notice detailing that the company has received (or has not received) certain types of secret warrants or gag orders.
-
Court Cases: Evidence of past court cases where the VPN was legally challenged but was genuinely unable to provide user data because they truly did not log it (e.g., the Turkish seizure of ExpressVPN servers). This is the strongest proof.
C. Independent Audits
To verify the claims of both jurisdiction and technology, seek out VPNs that have undergone independent third-party security audits. These audits, performed by reputable firms, verify that the VPN’s technical infrastructure and its no-logs policy are genuinely implemented and consistent with its privacy claims.
D. Payment Methods: Choosing Privacy-Focused Payment
To limit the digital trail that could connect your identity to your VPN account, choose providers that accept privacy-focused payment methods. Paying via cryptocurrencies (like Bitcoin) or anonymous gift cards prevents the VPN from collecting sensitive financial PII (Personally Identifiable Information) that could be seized in a legal investigation.
E. Server Locations vs. Headquarters: Focus on the Headquarters Jurisdiction First
Always prioritize the VPN's corporate headquarters/legal jurisdiction (Layer 1) over the physical location of the server you connect to (Layer 2). While a server in Iceland sounds secure, if the parent company is based in the US, the U.S. government can legally compel the company to compromise that Icelandic server. The legal home dictates the company's compliance obligations.
Conclusion:Jurisdiction is Paramount
The central thesis of this guide is clear: when selecting a Virtual Private Network, jurisdiction is paramount. The country where a VPN is legally headquartered determines the ultimate legal pressure it faces, overriding any technical promise of security or encryption. If a government can legally compel a company to log data or install backdoors, the user's privacy is already compromised. True digital security begins with choosing a legal haven outside of the aggressive surveillance reach of the 5, 9, and 14 Eyes alliances.
To ensure your digital safety, focus on providers that adhere to a verifiable set of best practices:
-
Safety in Law: Choose a VPN based in a jurisdiction with robust constitutional privacy protections and no mandatory data retention laws (e.g., Panama, the British Virgin Islands, or Switzerland).
-
Safety in Proof: Look for a proven No-Logs Policy, backed by real-world court cases where the provider had no data to surrender.
-
Safety in Verification: Select providers that have undergone comprehensive Independent Audits by reputable third-party security firms to verify their claims.
In the current era of ubiquitous surveillance, choosing a VPN is not just about unblocking streaming services; it is an act of digital responsibility. Your online data is valuable, and protecting it requires proactive choices. By understanding the critical role of legal jurisdiction, you empower yourself to make informed decisions that safeguard your personal information against both government overreach and corporate exploitation.
Frequently Asked Questions (FAQ)
Q: Why is a VPN's jurisdiction more important than its encryption?
A: Because laws trump technology. A VPN might use the strongest encryption, but if it is legally headquartered in a high-surveillance country (like a Five Eyes member), the government can legally compel the company to break its "no-logs" promise, monitor users, or surrender data via warrants and gag orders. The legal framework is the ultimate vulnerability.
Q: What exactly are the 'Five Eyes' and why should I avoid VPNs based there?
A: The Five Eyes (FVEY) is an intelligence alliance of the US, UK, Canada, Australia, and New Zealand. Member countries actively share surveillance data. You should avoid VPNs based there because these countries often have mandatory data retention laws and can use mutual legal assistance treaties (MLATs) or secret court orders to force VPNs to compromise user privacy.
Q: Does having a server in a safe country (like Iceland) protect me if the VPN company is based in the US?
A: No, the protection is limited. The company's legal home (headquarters jurisdiction) is the decisive factor. If the parent company is US-based (High-Risk), the US government can compel that company to compromise their servers located anywhere in the world (including Iceland). Always prioritize the headquarters jurisdiction first.
Q: What is a 'No-Logs Policy,' and how can I trust it?
A: A No-Logs Policy means the VPN promises not to collect or store any information that could identify a user's activities (e.g., browsing history, original IP addresses, connection timestamps). To trust it, look for two things:
-
Independent Audits: Third-party security firms verify the policy's technical implementation.
-
Proven Cases: Evidence from real-world events (like court cases or server seizures) where the company was unable to provide data because they genuinely had none.
Q: Which jurisdictions are considered the safest for VPN privacy?
A: The safest jurisdictions are those politically non-aligned and that have strong constitutional privacy laws and explicitly forbid mandatory data retention. Key examples include Panama, the British Virgin Islands (BVI), Switzerland, Romania, and Iceland.