OpenVPN, with its two-decade history, has long been the "gold standard" in the VPN industry. However, since its release in 2015, WireGuard has rapidly risen to prominence, threatening to replace OpenVPN, thanks to its extreme speed and minimalist codebase.
For users choosing a VPN service, the core dilemma is: which protocol offers the best speed, the most reliable security, and optimal privacy protection?
This article provides a comprehensive comparison of these two top-tier VPN protocols to help you determine the best connection method for your needs.
OpenVPN vs. WireGuard Overview
What is a VPN Protocol?
A VPN protocol is essentially the rulebook and the set of encryption standards that determine how your device connects securely to a VPN server. Think of it as the engine of your VPN—it decides how data is packaged, encrypted, and sent through the secure tunnel.
The protocol you choose is critical because it directly impacts three things:
-
Speed: How fast your connection is.
-
Stability: How often the connection drops.
-
Security: The strength of the encryption used.
OpenVPN
Introduced in 2001, OpenVPN quickly established itself as the industry standard for security and reliability.
-
Background: Creator James Yonan developed it to solve serious privacy issues he faced while traveling. It's an open-source project, which means its code is public and constantly checked by security experts for vulnerabilities.
-
Why it's Trusted: Its core strength is its flexibility and broad compatibility. It can run in either TCP (more reliable) or UDP (faster) modes and is compatible with virtually every major VPN provider, operating system, router, and firewall.
-
Best Use: OpenVPN is excellent for bypassing strict firewalls and getting around network restrictions due to its ability to disguise VPN traffic. For over a decade, it was considered the gold standard for secure connections.
WireGuard

Launched in 2015 by developer Jason Donenfeld, WireGuard was built to completely modernize VPN technology, offering a lean, high-speed alternative to older protocols.
-
The Speed Advantage: Its most defining feature is its minimal code base—only about 4,000 lines (compared to hundreds of thousands for OpenVPN). This lightweight design is the key to its blazing fast speeds and low data usage. Fewer lines of code also mean less area for security bugs, making it inherently secure.
-
Mandatory Modern Encryption: WireGuard uses a philosophy called "cryptographically opinionated." You can't choose your own encryption. It mandates the use of a fixed, modern set of algorithms (like ChaCha20 and Poly1305). This approach eliminates the risk of human error or accidentally choosing an outdated, weak encryption setting.
-
Current Status: WireGuard has rapidly become the protocol of choice for leading services (like NordVPN's custom NordLynx) due to its superior performance, though OpenVPN still holds the edge in native support for niche hardware like certain routers.
OpenVPN vs. WireGuard Pros and Cons (Quick User Decision)
|
Category |
OpenVPN |
WireGuard |
Winner |
Why? |
|
Speed & Efficiency |
High (UDP), Medium (TCP) |
Very High |
🥇WireGuard |
Smaller codebase, faster connection, extremely low data overhead. |
|
Security |
Excellent, Highly Flexible |
Excellent, Simple Architecture |
Tie |
Neither has known vulnerabilities, but WireGuard is easier to audit. |
|
Privacy & Logging |
Can be configured for no logs |
Requires IP storage by default |
🥇OpenVPN |
Easier to configure for no-logging by default. |
|
Bypassing Censorship |
Excellent |
Good |
🥇OpenVPN |
Native support for TCP 443 port, better for penetrating firewalls. |
|
Mobility/Network Switch |
Poor |
Excellent |
🥇WireGuard |
Can seamlessly handle switching between WiFi and cellular networks. |
|
Compatibility |
Very Broad |
Good |
🥇OpenVPN |
Supported by almost all VPN applications and most routers. |
Round 1: Speed, Latency, and Data Overhead (The WireGuard Efficiency Advantage)
In terms of speed and efficiency, WireGuard is undoubtedly the winner. If you need to perform latency-sensitive activities, such as online gaming or HD streaming, WireGuard is the superior choice.
1. Connection Speed and Latency (Ping)
Protocol speed is reflected not only in data transfer bandwidth but also in connection establishment speed (startup time) and connection latency (Ping value).
-
Startup Time: WireGuard excels. One study showed that an OpenVPN connection can take up to 8 seconds to fully establish, while a WireGuard connection usually takes only about 100 milliseconds. This fast reconnection capability is vital when a connection is lost or the tunnel is briefly interrupted.
-
Transfer Speed: Our test results align with other extensive performance assessments: WireGuard consistently surpasses OpenVPN in transfer speed by over 75%, and the speed difference can be nearly three times in short-distance server connections.
2. Bandwidth Efficiency and Data Overhead
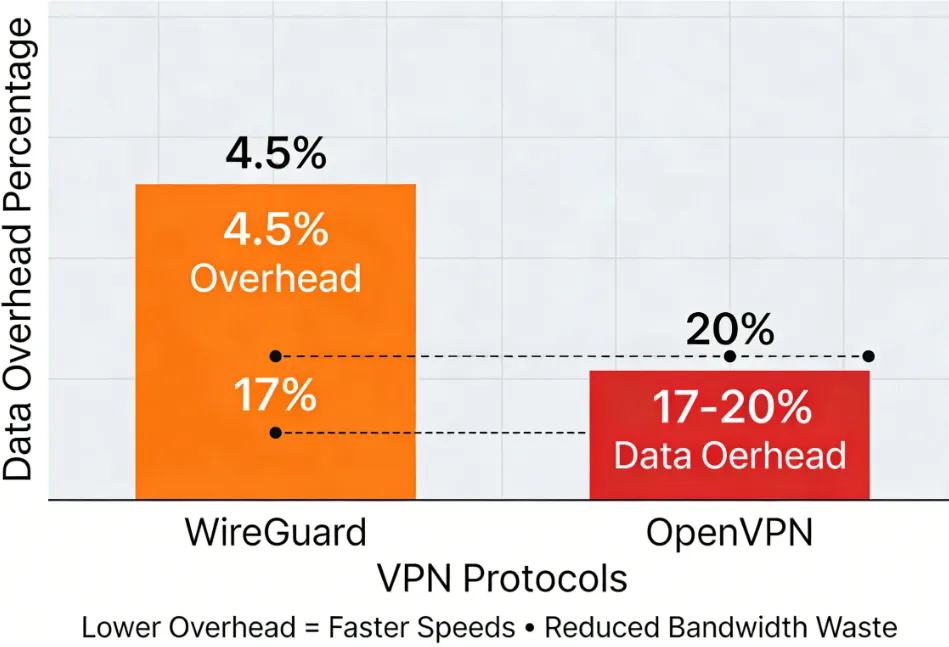
When transmitting user data, the VPN tunnel technology must add extra encapsulation information (header), and this additional traffic is referred to as data overhead or bandwidth loss. Controlling this overhead is crucial for users with data caps or those paying per-use on mobile data.
The choice of protocol directly determines the size of the data overhead. Our research indicates that WireGuard is far more data-efficient than OpenVPN:
-
Testing Method: We calculated the average data increment by copying a 209MB test file between two virtual servers and comparing it to the baseline without a VPN enabled.
-
Test Results: WireGuard's minimalist protocol encapsulation resulted in only 4.53% extra data, the lowest of all tested protocols. In contrast, OpenVPN's overhead is significantly higher:
-
OpenVPN (UDP) data increment reached 17.23%.
-
OpenVPN (TCP) bandwidth loss was even higher, close to 19.96%.
Conclusion: If your internet service has strict data limits, or you need to use a VPN over a mobile network, WireGuard will save you data and costs through its extremely low bandwidth consumption.
Round 2: Security, Encryption, and Code Auditability
Both OpenVPN and WireGuard perform excellently on core security metrics, and neither currently has any known security vulnerabilities. However, their approaches to achieving security differ significantly.
1. Encryption Algorithm Flexibility vs. Security
Cryptography here refers to the encryption algorithms and related primitives the protocol uses to ensure data cannot be read by unauthorized parties.
|
Feature |
OpenVPN |
WireGuard |
|
Encryption Algorithm Library |
OpenSSL (offers a wide range of choices) |
Fixed suite (built into the protocol) |
|
Key Cryptographic Primitives |
Encryption: AES, Blowfish, Camellia, ChaCha20, Poly1305, etc.; Hashing: SHA-256, etc.; Key Exchange: RSA, DSA, SM2, etc. |
Encryption & Authentication: ChaCha20-Poly1305; Hashing: BLAKE2s, SipHash24; Key Negotiation: Curve25519, HKDF. |
|
Transport Layer Flexibility |
Very high, can be configured for TCP or UDP to optimize speed and penetration in different network environments. |
Low, uses only the UDP protocol for transmission. |
|
Code Maturity |
Tested over 20 years, more mature |
Newer, but the algorithm itself (ChaCha20) is very secure |
OpenVPN's flexibility is its strength, allowing users or providers to choose the most suitable encryption suite. However, this flexibility also means it might be configured to use older, less secure cryptography.
WireGuard takes a "cryptographically opinionated" approach, utilizing only a modern and robust set of algorithms. While this limits choices, it eliminates the risk of using insecure code.
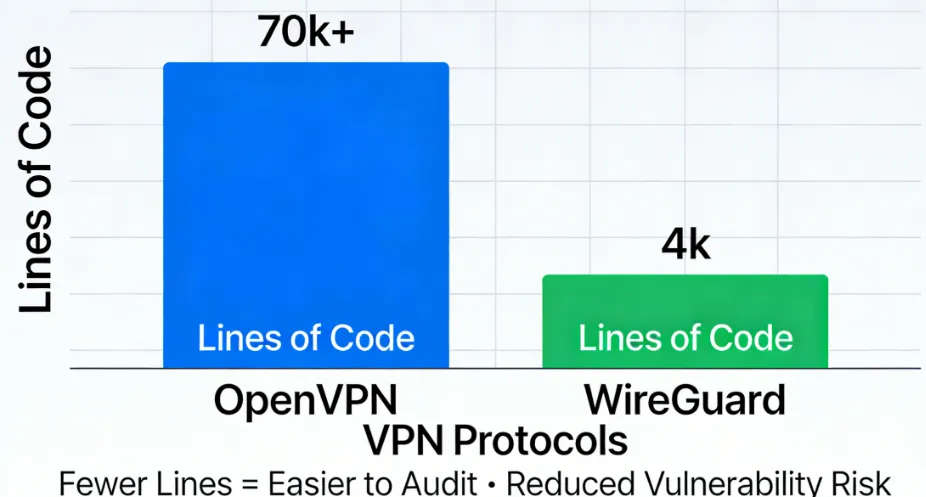
2. Codebase Size and Attack Surface - 🥇WireGuard
This is a key point where WireGuard leads technically:
-
WireGuard Codebase: Only about 4,000 lines.
-
OpenVPN Codebase: At least 70,000 lines.
WireGuard's smaller, more streamlined codebase means:
-
Easier to Audit: Security researchers can review WireGuard's code faster and more thoroughly, increasing the protocol's transparency and reliability.
-
Smaller Attack Surface: Less code means a lower possibility of potential bugs and security vulnerabilities.
Conclusion: Although both are secure, WireGuard's simple architecture gives it an edge in auditability and potential resistance to bugs.
Round 3: Censorship Bypass, Mobile Stability, and Compatibility
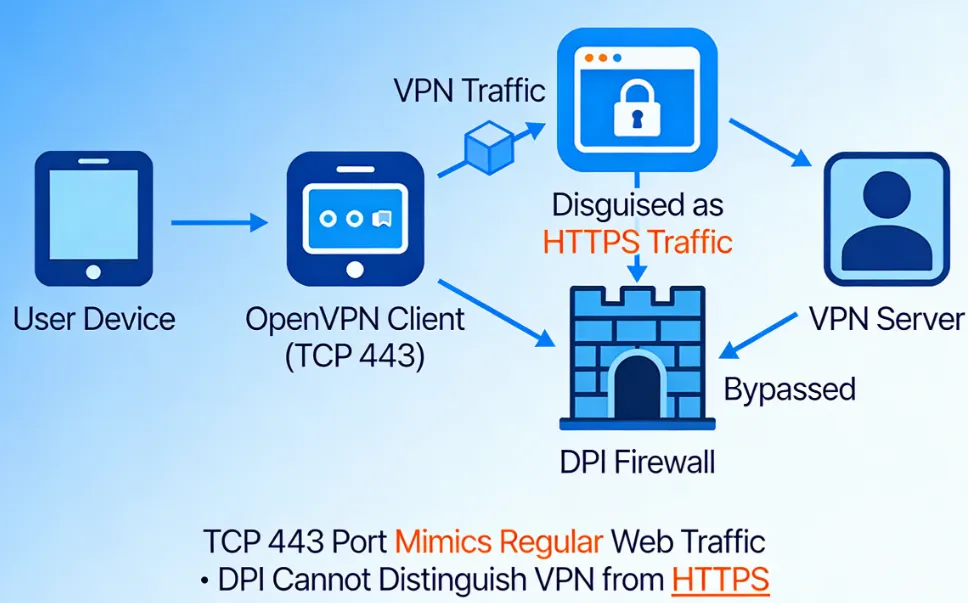
1. Bypassing Network Censorship and Firewall Penetration - 🥇OpenVPN
For users who need to break through severe network restrictions (such as in China, Iran, UAE, etc.), OpenVPN (TCP) is the first choice.
|
Protocol |
Penetration Power |
Key Advantage |
Reason |
|
OpenVPN (TCP) |
Extremely Strong |
Disguises itself as ordinary web traffic |
Native support for TCP 443 port, which is the same as encrypted web (HTTPS) traffic, making it difficult for censorship systems to block. |
|
WireGuard (UDP) |
Good |
Based only on UDP |
Slightly less effective against advanced firewalls, may be identified and blocked. |
OpenVPN (TCP) can disguise VPN traffic as regular web browsing, effectively bypassing Deep Packet Inspection (DPI). In real-world testing, VPN providers almost always default to OpenVPN when facing strict censorship.
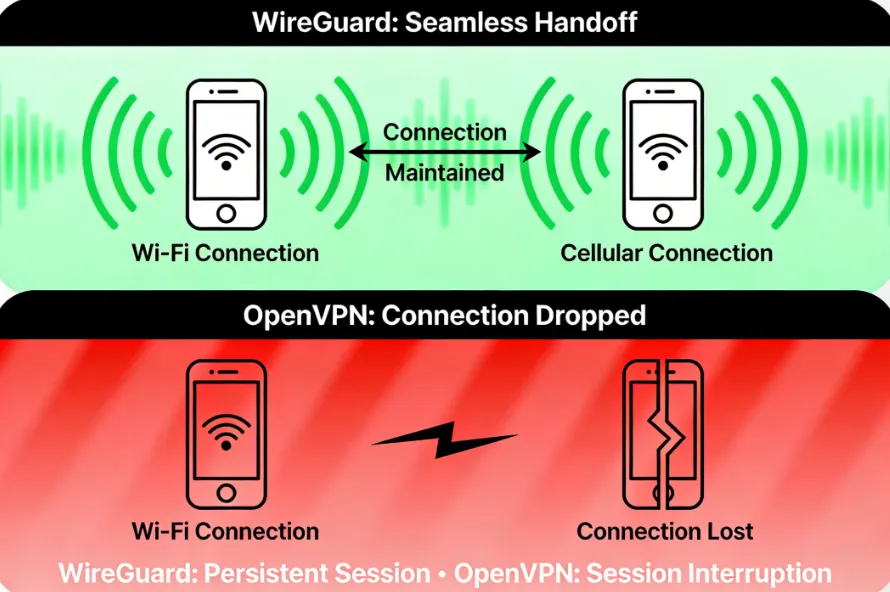
2. Mobility and Network Switching Performance - 🥇WireGuard
The ability of a protocol to maintain connection when a device's network environment changes (e.g., switching from Wi-Fi to cellular data) is called mobility.
WireGuard shows a remarkable advantage when frequently moving or switching between different network types.
-
Seamless Roaming: WireGuard can excellently and seamlessly handle everyday network environment changes, such as a user switching from home Wi-Fi to mobile data, or moving between different Wi-Fi hotspots. Its design ensures the VPN tunnel can be quickly and quietly re-established, minimizing connection interruptions.
-
OpenVPN's Weakness: OpenVPN performs poorly in this scenario, often leading to connection drops due to network address or port changes, requiring a longer time to fully recover.
For mobile roaming, WireGuard is generally best for speed/efficiency, while IKEv2/IPsec excels at stable network switching (Wi-Fi to cellular), making WireGuard or IKEv2/IPsec your top choices, with proprietary options like ExpressVPN's Lightway also great for seamless mobile transitions and battery saving. OpenVPN offers strong security but can be slower, and newer protocols often beat older ones like L2TP.
3. Platform Compatibility and Router Support - 🥇OpenVPN
A VPN protocol's ecosystem support and compatibility breadth determine which devices users can utilize it on. In this aspect, OpenVPN's historical advantage remains unchallenged.
Since its birth in 2001, OpenVPN's compatibility spans almost all existing operating systems and hardware platforms. Its advantages are mainly reflected in two areas:
-
Extensive System Support: OpenVPN not only supports modern mainstream systems (like Linux, Windows, macOS, iOS, and Android) but, more notably, it natively supports many old or niche operating systems, including Windows XP/Vista and Solaris, which is crucial for enterprise users maintaining legacy systems. WireGuard typically requires Windows 7 or higher.
-
Hardware and Router Support: OpenVPN has been integrated into the firmware of most routers and hardware firewalls. In contrast, WireGuard offers built-in support only on a few newer models or customized firmware routers, making OpenVPN the preferred choice for deploying VPNs at the network hardware level.
Although WireGuard appeared later, its adoption speed is extremely fast. It has been integrated into the desktop and mobile applications of most mainstream VPN service providers, often provided as the default option, such as NordVPN's NordLynx.
Protocol Support Overview of Mainstream VPN Service Providers:
|
VPN Service Provider |
OpenVPN Support |
WireGuard Support |
|
ExpressVPN |
✓ |
✓ |
|
NordVPN |
✓ |
✓ |
|
CyberGhost |
✓ |
✓ |
|
IPVanish |
✓ |
✓ |
|
Surfshark |
✓ |
✓ |
|
PrivateVPN |
✓ |
✗ |
|
PIA |
✓ |
✓ |
|
Windscribe |
✓ |
✓ |
|
Proton VPN |
✓ |
✓ |
|
Astrill |
✓ |
✓ |
Conclusion: WireGuard is quickly catching up, but if you need to configure a VPN on various platforms (especially older systems) or routers, OpenVPN is currently the most broadly compatible and reliable choice.
4. IP Logging & Privacy: WireGuard's IP Storage Challenge vs. OpenVPN's Simplicity
The core value of a VPN lies in protecting user privacy, and the protocol's behavior when handling user IP addresses is crucial.
|
Feature |
OpenVPN |
WireGuard |
|
Default Logging Behavior |
Default verbose configuration records real IP addresses |
Default requires storing user IP addresses until the server restarts |
|
Ease of Configuration |
Easy to achieve no-logging by adjusting verbosity or configuring information clearance. |
Requires special workarounds by the VPN service provider to achieve no-logging. |
OpenVPN and Logging Flexibility: While OpenVPN's default configuration is set to log information like usernames and IP addresses, VPN providers can very easily and directly stop this by simply dropping the server-side logging level to "level 0." This ability to flexibly configure the logging level is a key advantage for providers aiming for a simple, explicit no-log setup.
WireGuard's Privacy Challenge: WireGuard's architecture is designed in a way that inherently requires the server to store the user's real IP address throughout the session and until the server is actually restarted. This retention is viewed as a built-in privacy risk, as a compromised server could expose these IPs, potentially allowing user activity to be traced.
Commercial Workarounds for WireGuard
To overcome this architectural limitation and maintain a strict no-log policy, major commercial VPN providers implement specific strategies:
-
Double NAT (NordLynx): Services like NordVPN's NordLynx employ Double Network Address Translation. This method never stores the user's static IP. Instead, it assigns a temporary, dynamic IP for the session, deleting the temporary IP immediately once the connection ends. Double NAT (Network Address Translation) with WireGuard happens when you have two routers (e.g., ISP modem/router + your own router), creating two private network layers, which complicates direct connections, port forwarding, and VPNs by making devices appear behind multiple private IPs. While WireGuard can often handle this, it might require specific configurations like using KeepAlives, setting DMZs on the first router, or running a cloud server as a middleman (NAT traversal) to establish reliable peer-to-peer communication, as both NAT layers translate addresses, adding complexity and potential delays.
-
Time-Limited Deletion: Other providers, such as Mullvad and IVPN, configure their servers to automatically wipe the stored IP address after a very short period of inactivity (typically 3 to 10 minutes).
Conclusion: In summary, configuring OpenVPN for no-logging is technically simpler and more direct. However, the ultimate protection is consistent: as long as you choose a reputable VPN provider committed to a no-log policy and utilizing the mitigation measures described above (especially for WireGuard), your privacy remains secure regardless of which protocol you choose.
Conclusion: Choosing the Best VPN Protocol Based on Your Needs
|
Your Need is to... |
Recommended Protocol |
Reason |
|
Pursue extreme speed and efficiency |
WireGuard |
Fastest speed, quick connection, and minimal data overhead. |
|
Use routers or old devices |
OpenVPN |
Broadest compatibility, supports almost all platforms and devices. |
|
Bypass nation-state censorship |
OpenVPN (TCP) |
Can disguise itself as HTTPS traffic, effectively penetrating firewalls. |
|
Prioritize auditability |
WireGuard |
Extremely small codebase, easier for security experts to verify. |
|
Value privacy in default configuration |
OpenVPN |
Protocol is easier to configure for zero logs. |
Frequently Asked Questions (FAQ)
Q1: Is WireGuard really faster than OpenVPN?
A: Yes.
WireGuard's codebase is very lean (about 4,000 lines), which results in much faster connection establishment, extremely low data overhead (only about 4.53%), and consequently, significantly higher transfer speeds and lower latency.
Q2: Which protocol is better for security?
A: Both are highly secure, and neither has known vulnerabilities.
OpenVPN is time-tested; WireGuard is easier to audit and has a smaller attack surface due to its smaller codebase. Both are top-tier secure choices.
Q3: Which protocol is better for mobile users?
A: WireGuard is better for mobile users.
It seamlessly handles changes in network environments (like switching from Wi-Fi to mobile data), offering stable connections that are less prone to disconnections than OpenVPN.
Q4: Which protocol should I use to bypass strict network censorship (like firewalls)?
A: The TCP mode of OpenVPN is recommended.
OpenVPN (TCP) can disguise VPN traffic as normal HTTPS web traffic by using port 443, making it more effective in penetrating Deep Packet Inspection (DPI) firewalls.
Q5: Does WireGuard log my real IP address?
A: WireGuard's native design requires storing IP addresses on the server until the server is restarted.
However, most reputable commercial VPN services use special workarounds (like Double NAT or time-limited deletion) to protect user privacy, so it is generally safe in practice.
Q6: If I need to set up a VPN on a router or an old device, which one should I choose?
A: You should choose OpenVPN.
It has the broadest compatibility; almost all router firmware and older operating systems natively support OpenVPN, while WireGuard's support is still limited.