What is a VPN Protocol?
A VPN protocol is a set of rules and instructions that define how a Virtual Private Network (VPN) connection is established and maintained. Essentially, it determines the following critical factors for the secure tunnel between your device and the VPN server:
-
Encapsulation: How your data packets are wrapped up (encapsulated) for transport.
-
Encryption: The specific cryptographic algorithms (like AES-256) used to scramble the data to ensure confidentiality.
-
Authentication: The methods used to verify the identity of both the client (your device) and the server to prevent man-in-the-middle attacks.
-
Key Exchange: The process by which the client and server securely generate and agree upon the secret keys used for encryption.
The protocol you choose fundamentally impacts the performance, stability, and security of your VPN connection. Different protocols are optimized for different priorities—for instance, IKEv2/IPsec excels at stability and speed on mobile networks, while WireGuard prioritizes extreme speed due to its minimalist code base.
What is the IKEv2/IPsec Protocol?
The IKEv2/IPsec protocol suite is the modern standard for establishing secure VPN (Virtual Private Network) connections. It is a fusion of two distinct, yet dependent, protocols: Internet Key Exchange version 2 (IKEv2) and Internet Protocol Security (IPsec).
IPsec is the foundational framework responsible for encrypting and encapsulating the data packets—the mechanism that performs the actual tunneling and data protection. However, IPsec requires securely generated cryptographic keys and Security Associations (SAs) to function.
This is where IKEv2 comes in. IKEv2 is an agile, streamlined signaling protocol, standardized by Microsoft and Cisco, designed to negotiate, create, and efficiently maintain these Security Associations between two endpoints. Compared to its predecessor, IKEv1, it uses fewer messages to establish a connection, dramatically increasing speed and reducing latency.
The Mobile-First Advantage
IKEv2 is often referred to as a "mobile-first" protocol due to its reliance on the MOON (Mobility and Multihoming) extension. This feature is crucial for maintaining connection stability and speed, particularly when a user switches between network types (e.g., moving from Wi-Fi to cellular data) or temporarily loses connection. IKEv2's fast rekeying and SA regeneration capabilities ensure the VPN tunnel recovers quickly and reliably, making it the preferred choice for modern mobile devices and remote work environments.
What is IKEv2?
IKEv2 (Internet Key Exchange version 2) is the crucial signaling protocol responsible for key management in the IPsec suite. It operates in two phases to efficiently establish and maintain a secure channel between VPN endpoints:
-
Phase 1 (IKE SA Establishment): This phase securely negotiates and establishes the initial secure tunnel, known as the IKE Security Association (IKE SA). This tunnel is used to protect the subsequent key exchange messages. Strong authentication methods, such as pre-shared keys (PSK), digital certificates, or EAP (Extensible Authentication Protocol), are used here.
-
Phase 2 (Child SA Establishment): Once the IKE SA is established, this phase rapidly creates the "Child Security Associations" (Child SAs), which contain the keys and algorithms specifically needed by IPsec to encrypt and authenticate the actual user data traffic.
IKEv2 is highly efficient and resilient. It dramatically reduces the number of messages required for setup compared to IKEv1, speeding up connection times. Its built-in support for mobility (via MOON/MOBIKE) also allows the tunnel to quickly re-establish itself after a brief network disconnection without having to restart the entire negotiation process.
What is IPsec?
IPsec (Internet Protocol Security) is not a single protocol, but a suite of protocols that secures IP communications by authenticating and/or encrypting every IP packet. It operates directly at the Network Layer (Layer 3 of the OSI model) and provides two fundamental security services for data:
-
Authentication Header (AH): Provides data origin authentication and connectionless integrity for the IP packet. It guarantees that the data received is exactly the data sent and comes from the expected source.
-
Encapsulating Security Payload (ESP): Provides confidentiality (encryption), data origin authentication, connectionless integrity, and an anti-replay service. ESP is the most commonly used component as it performs the actual data concealment.
IPsec functions in two primary modes: Tunnel Mode and Transport Mode. In VPNs, Tunnel Mode is used, where the original IP packet is entirely encapsulated and protected by a new IP header, effectively "tunneling" the private data across a public network.
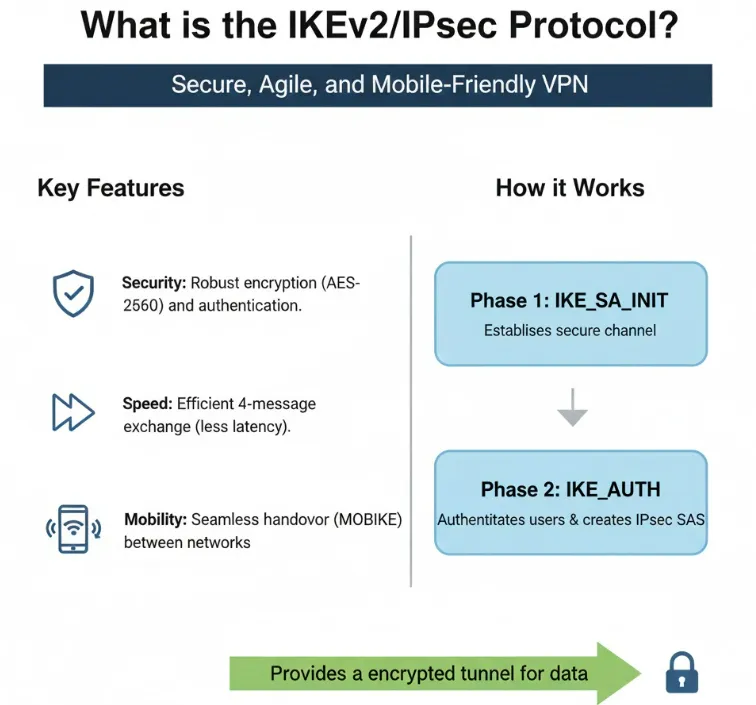
How Does IKEv2/IPsec Work?
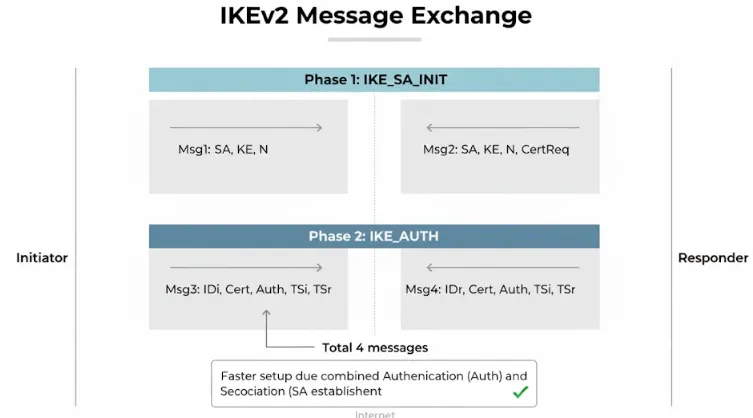
The successful operation of the IKEv2/IPsec suite relies on a highly efficient, four-message handshake process that establishes the necessary cryptographic context before any user data is transmitted. This process is divided into two logical phases:
Phase 1: IKE SA Initialization (The Secure Control Channel)
This phase’s sole purpose is to establish a secure, authenticated control channel between the two VPN endpoints. This channel, the IKE Security Association (IKE SA), protects all subsequent negotiation messages.
-
IKE_SA_INIT (2 Messages): The initiator and responder exchange cryptographic proposals (e.g., encryption algorithms, hash functions) and perform the Diffie-Hellman key exchange. Diffie-Hellman ensures Perfect Forward Secrecy (PFS) by generating a shared secret key that has not been transmitted over the network.
-
IKE_AUTH (2 Messages): The endpoints authenticate each other using the protected channel established in the first step. Authentication can be performed via digital certificates, Pre-Shared Keys (PSK), or EAP. Once authenticated, the first Child SA is often established simultaneously, bundling the key generation and authentication steps for speed.
Phase 2: Child SA Creation and Data Protection (The Data Tunnel)
With the secure IKE SA established, the endpoints can now quickly create one or more Child Security Associations (SAs) needed for IPsec to protect the data itself.
-
CREATE_CHILD_SA (Optional): Additional Child SAs can be created, negotiated, or rekeyed at any time using only two messages, making the process extremely fast. The Child SA specifies the exact parameters (such as the encryption algorithm, like AES-GCM, and the integrity check, like HMAC-SHA256) that will be applied to the data.
Once a Child SA is in place, IPsec takes over. Data packets are encrypted and encapsulated using the Encapsulating Security Payload (ESP) protocol in Tunnel Mode. The IPsec tunnel uses the negotiated key material from IKEv2 to provide confidentiality, integrity, and origin authentication for the user’s traffic.
Main Benefits of IKEv2/IPsec
IKEv2/IPsec has become the preferred choice for modern VPN solutions, largely due to its blend of high performance and robust security features, particularly benefiting mobile users.
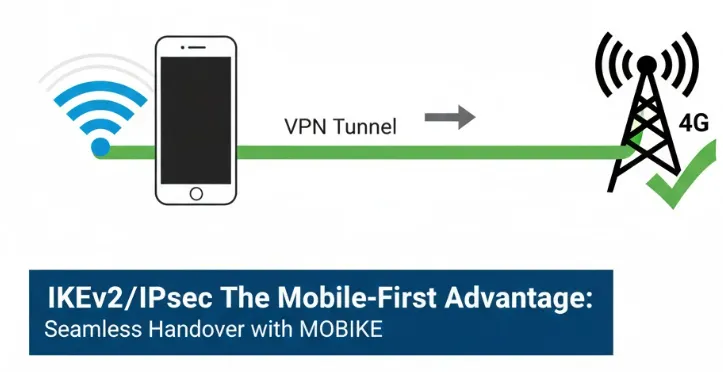
1. Unmatched Stability: How MOON/MOBIKE Delivers Seamless Mobile VPN Connectivity
This is the defining feature of IKEv2. The Mobility and Multihoming (MOBIKE) extension allows the VPN tunnel to withstand changes in the client’s network connection without dropping the session. This is critical for mobile devices that frequently switch between Wi-Fi hotspots, cellular data, or experience temporary signal loss. The fast re-establishment process ensures near-instantaneous reconnection and continuity of data transfer.
- IP Address Agility: When a mobile device changes networks, it typically gets a new IP address. Without MOBIKE, the VPN connection would drop because the original IP address used to establish the tunnel is no longer valid.
- Session Persistence: MOBIKE allows the VPN client to notify the VPN gateway of its new IP address using a specific message within the existing, secure tunnel. The gateway can then update the connection parameters on the fly.
- Zero-Interruption Handovers: This mechanism ensures that the transition between networks is fast and typically results in minimal interruption time for the user's data flow. This is particularly crucial for applications that require continuous connectivity, such as real-time communication, streaming, or critical enterprise applications used by mobile workforces (e.g., public safety officers using secure apps in the field).
2. Enhanced Performance and Speed
IKEv2 uses a highly streamlined four-message exchange to establish the connection, significantly reducing the overhead and latency compared to the nine messages required by IKEv1. This efficiency translates directly into faster connection times and better overall throughput, making the user experience smoother and less noticeable.
3. Cryptographic Strength: IKEv2 and Perfect Forward Secrecy (PFS)
As part of the IPsec suite, IKEv2 supports the use of strong, modern cryptographic primitives. It mandates the use of Diffie-Hellman key exchange, which provides Perfect Forward Secrecy (PFS). This means that if a long-term key (like a digital certificate) is compromised in the future, past session keys remain secure and encrypted traffic cannot be decrypted.
Why "Perfect" Key Separation is Critical: The "perfect" aspect stems from the fact that each session's key is a unique, temporary shared secret that is computationally independent of the server's long-term private key and other session keys.
4. Broad Platform Support
Developed jointly by Microsoft and Cisco, IKEv2 has been widely adopted across major operating systems. It is often natively supported by Windows, macOS, iOS, and Android devices, simplifying deployment and configuration for end-users by removing the need for third-party client software.
The dual-parentage of IKEv2/IPsec (developed by Microsoft and Cisco) presents a unique trust dynamic compared to other protocols. While its widespread adoption and corporate backing lend it undeniable stability and extensive auditing within the industry, the core specifications and proprietary implementations are not fully open-source in the same manner as protocols like OpenVPN. This difference in transparency is a point of contention for some security experts, who favor OpenVPN's public, fully auditable code base, or WireGuard’s minimalist design, which significantly simplifies external security review. For most enterprise and mobile users, the industry backing, native OS integration, and mature implementation of IKEv2 often outweigh the desire for full public source code access.
5. Dead Peer Detection (DPD)
IKEv2 includes robust support for Dead Peer Detection. This mechanism allows endpoints to quickly detect when the other side of the connection has failed or become unreachable. This allows the system to terminate the session efficiently, conserving resources and preventing orphaned connections that can pose a security risk.
Main Disadvantages of IKEv2/IPsec
The main disadvantages of IKEv2/IPsec are its potential for blocking on restrictive firewalls (due to fixed UDP ports 500/4500), complicated manual setup on some devices (especially older ones/Linux), closed-source nature raising trust concerns, and potential compatibility issues with older systems, despite its strong mobile performance and modern encryption.
1. Firewall & Network Blocking: Uses UDP ports 500 & 4500, which network admins often block, hindering connectivity.
2. Setup Complexity: Can be complex on non-standard devices (like some Android/Linux) needing manual steps, unlike Windows/macOS.
3. Closed Source: Developed by Microsoft/Cisco, its closed-source nature contrasts with open-source alternatives like OpenVPN/WireGuard, affecting transparency.
4. Compatibility Issues: Not natively supported on all older devices or routers, requiring extra work.
5. Security Concerns (Perceived/Historical): While generally secure, its Microsoft/Cisco origins and past NSA claims (exploiting IKE) raise trust issues for some.
6. Packet Size/Fragmentation: IKEv2 packets can become large, potentially causing issues.
IKEv2 vs OpenVPN vs WireGuard: Performance, Stability, and Security Comparison
Determining if IKEv2/IPsec is "better" depends heavily on the specific use case, as each major VPN protocol has distinct strengths. However, IKEv2/IPsec is consistently ranked among the top due to its combination of speed, stability, and security assurances.
|
Feature |
IKEv2/IPsec |
OpenVPN |
WireGuard |
|
Mobility & Stability |
Excellent (Native MOBIKE). Fast reconnections, ideal for mobile devices. |
Good, but depends on client configuration and transport (TCP/UDP). Slower to reconnect. |
Good, uses persistent connection logic, but less widely tested than MOBIKE. |
|
Speed & Performance |
Very Fast. Efficient four-message handshake. Less overhead than OpenVPN. |
Moderate. Can be slower due to relying on the TCP/TLS stack. |
Extremely Fast. Minimal code base and runs in kernel space (Linux, macOS). |
|
Security Standard |
High. Mandatory PFS and supports modern algorithms (AES-GCM). Heavily audited. |
High. Uses strong cryptography and SSL/TLS standards. Highly configurable. |
High (But Opinionated). Uses modern, fixed ciphers (ChaCha20, Poly1305), reducing configuration errors. |
|
Native Support |
Broad. Built into Windows, macOS, iOS, and others. |
None. Requires third-party client or dedicated configuration. |
Growing. Now included in modern Linux kernels, but external clients needed for most platforms. |
|
Portability |
Excellent. The standardized nature ensures consistent implementation. |
Moderate. The reliance on OpenSSL libraries can sometimes cause platform-specific issues. |
Excellent. The small code base makes it easily auditable and portable. |
Key Comparisons:
-
IKEv2/IPsec vs. OpenVPN: IKEv2/IPsec is generally faster and significantly more stable for mobile users who frequently change networks, thanks to MOBIKE. OpenVPN is praised for its ability to use TCP port 443, making it better at bypassing firewalls and network restrictions, where IKEv2/IPsec (usually UDP port 500/4500) might be blocked.
-
IKEv2/IPsec vs. WireGuard: WireGuard represents the new generation of VPNs, offering superior speed and a vastly smaller code base (making it easier to audit for bugs). While IKEv2/IPsec is a mature, thoroughly tested protocol with native support across almost every OS, WireGuard is gaining popularity quickly, though its fixed cipher suite and relative youth mean IKEv2/IPsec still holds the title for most widely adopted and enterprise-trusted mobile-first protocol.
Conclusion: IKEv2/IPsec excels in environments demanding high stability and native integration, particularly in the corporate and mobile sectors. Its maturity and native OS support give it an edge in deployment simplicity over OpenVPN, and its tried-and-true robustness makes it a safer, if slightly slower, choice than the emerging WireGuard.
IKEv2/IPsec Configuration Guide: Server-Side (StrongSwan) and Client Setup
Configuring an IKEv2/IPsec VPN involves two main components: setting up the VPN server (or gateway) and configuring the client device. Since IKEv2 is often natively supported, the client configuration is usually straightforward.
1. Server-Side Configuration (VPN Gateway)
The server must be set up to listen for IKEv2 connections (typically UDP ports 500 and 4500) and define the cryptographic policies. This usually involves specialized software like StrongSwan (Linux/Unix) or the native services on a firewall/router appliance.
Key Server Steps:
-
Define IKE SA Parameters (Phase 1):
-
IKE Version: Specify IKEv2.
-
Authentication Method: Choose between Certificates (Recommended for enterprise) or Pre-Shared Key (PSK). Certificates offer stronger, more scalable security.
-
Encryption & Hash: Define the algorithms for the control tunnel (e.g., AES-256 GCM for encryption, SHA-256 for hashing).
-
Diffie-Hellman Group: Select a strong group (e.g., Group 14 or higher) for Perfect Forward Secrecy.
-
Define Child SA Parameters (Phase 2):
-
Traffic Selector: Define the networks that will be tunneled (e.g., 0.0.0.0/0 for full tunnel, or a specific internal subnet).
-
Encryption & Integrity: Define the algorithms for the data tunnel (e.g., AES-256 GCM).
-
User/Client Management:
-
Create user accounts or manage the certificate distribution needed for client authentication.
-
Configure the IP pool from which clients will receive their internal IP addresses.
-
Firewall Rules: Ensure the server's firewall allows inbound UDP traffic on ports 500 and 4500.
2. Client-Side Configuration (User Device)
Since IKEv2 is natively integrated into most operating systems, the configuration is typically done through the network settings menu, minimizing the need for third-party apps.
General Client Configuration Steps (Example: Windows/macOS/iOS):
-
Select VPN Type: Navigate to the network settings or VPN settings and choose to "Add VPN" or "Add Configuration."
-
Set Protocol: Select the VPN type as "IKEv2" or "IKEv2/IPsec."
-
Enter Server Information:
-
Server Address: Enter the public IP address or hostname of the VPN server.
-
Remote ID / Local ID (Optional): These fields are sometimes required when using certificates for identity verification.
-
Set Authentication Method:
-
If PSK: Enter the Pre-Shared Key (sometimes called the "Shared Secret").
-
If Username/Password (EAP): Enter the user credentials.
-
If Certificate: Import the required client certificate file into the device's certificate store and select it for authentication.
-
Connect: Save the configuration and attempt to connect. The client will initiate the four-message IKEv2 handshake to establish the secure tunnel.
Troubleshooting Tip: If a connection fails, the issue is almost always a mismatch in Phase 1 or Phase 2 parameters (like encryption type or DH Group) between the server and the client. Always verify the configured cryptographic proposals on both sides.
Frequently Asked Questions (FAQ)

This section addresses common questions about the IKEv2/IPsec protocol suite, its security, and its practical use.
Q1: Is IKEv2 the same as IPsec?
A: No, they are not the same but they are dependent protocols. IKEv2 (Internet Key Exchange version 2) is the key management and signaling protocol. Its job is to securely establish the connections (Security Associations or SAs) and manage the cryptographic keys. IPsec (Internet Protocol Security) is the data protocol suite that uses the keys and SAs created by IKEv2 to encrypt and authenticate the actual user data traffic. IKEv2 is the locksmith, and IPsec is the secure lock.
Q2: What ports does IKEv2/IPsec use?
A: IKEv2/IPsec primarily uses UDP port 500 for the initial key exchange (Phase 1). If the client is behind a NAT (Network Address Translation) device, it uses UDP port 4500 for NAT traversal (NAT-T), which encapsulates the IKE messages in UDP packets to allow them through firewalls. For the IPsec data tunnel itself, the Encapsulating Security Payload (ESP) protocol is used, which is IP Protocol Number 50 (not a UDP or TCP port number).
Q3: Does IKEv2/IPsec support Perfect Forward Secrecy (PFS)?
A: Yes, PFS is a mandatory feature of IKEv2. Perfect Forward Secrecy ensures that the key used to protect one session (the Child SA keys) is not derived from any other key and is unique to that session. Critically, it ensures that if the main long-term authentication key (like a certificate) is ever compromised, a past session key cannot be retroactively used to decrypt recorded traffic. This is accomplished using the Diffie-Hellman key exchange during Phase 1.
Q4: Why is IKEv2 considered "mobile-first"?
A: IKEv2 is considered mobile-first primarily because of its MOBIKE (Mobility and Multihoming Protocol and Extensions) support. MOBIKE allows a VPN client to change its network connection (e.g., switching from Wi-Fi to cellular data, or moving between Wi-Fi networks) without dropping the established VPN tunnel. It quickly re-establishes the connection using the new IP address, ensuring sessions remain active and continuous, which is essential for mobile device users.
Q5: Can firewalls easily block IKEv2/IPsec?
A: Yes, IKEv2/IPsec can be more easily blocked than protocols like OpenVPN. Since IKEv2 typically uses fixed UDP ports (500 and 4500), network administrators and firewalls can simply block these ports to prevent VPN connections. OpenVPN, by contrast, can be configured to use TCP port 443, making it appear as standard HTTPS traffic, which is rarely blocked. This is a primary disadvantage of IKEv2/IPsec in highly restricted networks.
PS: All images in this article are sourced from the merchant's official website and are copyrighted by the merchant.